
Computers and Technology, 04.03.2021 02:00 NetherisIsTheQueen
In Chapter 4, we developed an algorithm for converting from binary to decimal. You can generalize this algorithm to work for a representation in any base. Instead of using a power of 2, you will write a program that converts any base between 2 and 16. Recall that for numbers 10 - 15 we use letters A - F.
In convert. py, define a function named repToDecimal that expects two arguments, a string, and an integer. The second argument should be the base. For example, repToDecimal("10", 8) returns 8, whereas repToDecimal("10", 16) returns 16.
The function should use a lookup table to find the value of any digit. Make sure that this table (it is actually a dictionary) is initialized before the function is defined.
For its keys, use the 10 decimal digits (all strings) and the letters A . . . F (all uppercase). The value stored with each key should be the integer that the digit represents. (The letter A associates with the integer value 10, and so on.)
The main loop of the function should convert each digit to uppercase, look up its value in the table, and use this value in the computation.
A main function that tests the conversion function with numbers in several bases has been provided.
An example of main and correct output is shown below:
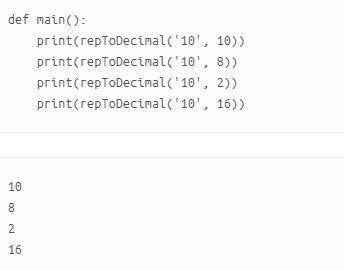

Answers: 3


Another question on Computers and Technology

Computers and Technology, 23.06.2019 07:50
Most shops require the technician to enter a starting and ending time on the repair order to track the actual time the vehicle was in the shop and closed out by the office. this time is referred to as _ time ? a. comeback b. ro c. cycle d. lead
Answers: 1

Computers and Technology, 23.06.2019 11:30
Auser is given read permission to a file stored on an ntfs-formatted volume. the file is then copied to a folder on the same ntfs-formatted volume where the user has been given full control permission for that folder. when the user logs on to the computer holding the file and accesses its new location via a drive letter, what is the user's effective permission to the file? a. read b. full control c. no access d. modify e. none of the above
Answers: 1

Computers and Technology, 24.06.2019 00:00
Afashion designer wants to increase awareness about her brand. which network can she use and why she can use the blank to blank her products online. answers for the first blank: internet, extranet, or intranet answers for the second blank: market, design, and export
Answers: 1

Computers and Technology, 24.06.2019 06:30
Some peer-to-peer networks have a server and some don't. true false
Answers: 2
You know the right answer?
In Chapter 4, we developed an algorithm for converting from binary to decimal. You can generalize th...
Questions




Biology, 13.07.2021 22:50





Mathematics, 13.07.2021 22:50



Biology, 13.07.2021 22:50








Mathematics, 13.07.2021 22:50



