
Computers and Technology, 24.02.2021 19:50 janyiareese12
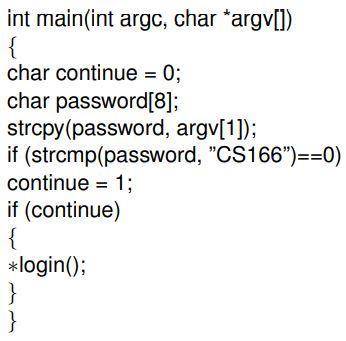
Consider the following piece of C code (in attachment):
In the above code, ∗login() is a pointer to the function login()
(In C, one can declare pointers to functions which means that the
call to the function is actually a memory address that indicates
where the executable code of the function lies). (1) Is this
code vulnerable to a buffer-overflow attack with reference to the
variables password[] and continue? If yes, describe how an attacker
can achieve this and give an ideal ordering of the memory cells
(assume that the memory addresses increase from left to right)
that correspond the variables password[] and continue of the code
so that this attack can be avoided. (2) To fix the problem, a security
expert suggests to remove the variable continue and simply use
the comparison for login. Does this fix the vulnerability? What
kind of new buffer overflow attack can be achieved in a multiuser
system where the login() function is shared by a lot of users (both
malicious and and nonmalicious) and many users can try to log
in at the same time? Assume for this question only (regardless
of real systems’ behavior) that the pointer is on the stack rather
than in the data segment, or a shared memory segment. (3) What
is the existing vulnerability when login() is not a pointer to the
function code but terminates with a return() command? Note that
the function strcpy does not check an array’s length.

Answers: 3


Another question on Computers and Technology

Computers and Technology, 22.06.2019 12:20
Usually, when we sniff packets, we are only interested certain types of packets. we can do that by setting filters in sniffing. scapy’s filter use the bpf (berkeley packet filter) syntax; you can find the bpf manual from the internet. set the following filters and demonstrate your sniffer program again (each filter should be set separately): (a) capture only the icmp packet. (b) capture any tcp packet that comes from a particular ip and with a destination port number 23. (c) capture packets comes from or to go to a particular subnet. you can pick any subnet, such as 128.230.0.0/16; you should not pick the subnet that your vm is attached to.
Answers: 3


Computers and Technology, 24.06.2019 00:20
The guy wire bd exerts on the telephone pole ac a force p directed along bd. knowing the p must have a 720-n component perpendicular to the pole ac, determine the magnitude of force p and its component along line ac.
Answers: 2

Computers and Technology, 24.06.2019 13:30
What is the most important for you to choose before you build a network?
Answers: 1
You know the right answer?
Consider the following piece of C code (in attachment):
In the above code, ∗login() is a pointer to...
Questions



Biology, 20.05.2021 15:20

Arts, 20.05.2021 15:20



Social Studies, 20.05.2021 15:20




Mathematics, 20.05.2021 15:20

English, 20.05.2021 15:20

Mathematics, 20.05.2021 15:20







Mathematics, 20.05.2021 15:20



