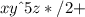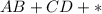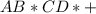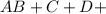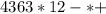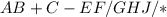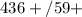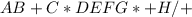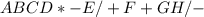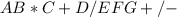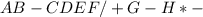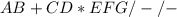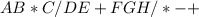Conversion To Postfix
EXAMPLE: A+(B*C-(D/E-F)*G)*H
Stack Input Output
Empty A+(B*C-(D/E...

Computers and Technology, 15.02.2021 20:40 chelsey54
Conversion To Postfix
EXAMPLE: A+(B*C-(D/E-F)*G)*H
Stack Input Output
Empty A+(B*C-(D/E-F)*G)*H -
Empty +(B*C-(D/E-F)*G)*H A
+ (B*C-(D/E-F)*G)*H A
+ ( B*C-(D/E-F)*G)*H A
+ (*C-(D/E-F)*G)*H AB
+ (* C-(D/E-F)*G)*H AB
+ (* -(D/E-F)*G)*H ABC
+ (-(D/E-F)*G)*H ABC*
+ (-(D/E-F)*G)*H ABC*
+ (-(/E-F)*G)*H ABC*D
+ (-(/E-F)*G)*H ABC*D
+ (-(/-F)*G)*H ABC*DE
+ (-(- F)*G)*H ABC*DE/
+ (-(- F)*G)*H ABC*DE/
+ (-(-)*G)*H ABC*DE/F
+ (- *G)*H ABC*DE/F-
+ (-*G)*H ABC*DE/F-
+ (-* )*H ABC*DE/F-G
+ *H ABC*DE/F-G*-
+* H ABC*DE/F-G*-
+* End ABC*DE/F-G*-H
Empty End ABC*DE/F-G*-H*+
Convert the following Infix Expression to Postfix, Using the above sample solution
The infix expression. x^y/(5*z)+2
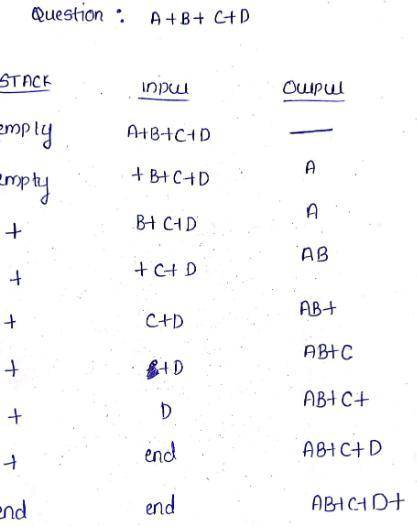
A + B * C + D
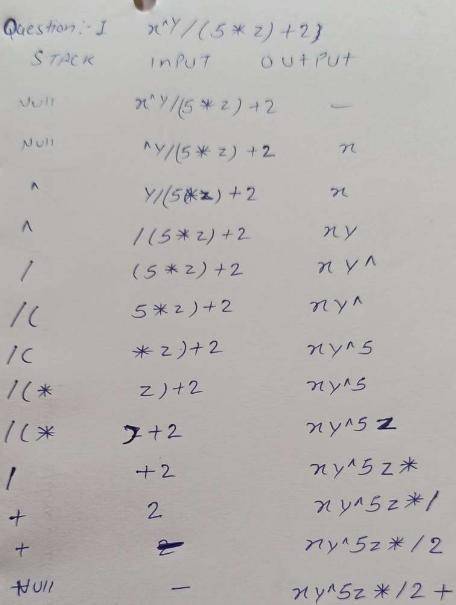
(A + B) * (C + D)
A * B + C * D
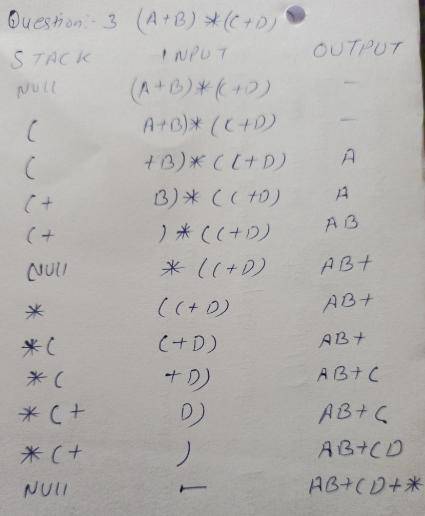
A + B + C + D
6. 4 + 3 * (6 * 3 - 12)
7. (A + B - C) * (E / F) – (G – H / J)
8. 4 / (3 + 6) + 59
9. (A + B) * C + D / (E + F * G) – H
10. A + ((B - C * D) / E ) + F - G / H
11. (A * B + C) / D - E / (F + G)
12. A - B - C * (D + E / F - G) – H
13. (A + B) - C * D / (E - F / G)
14. A * B / C + (D + E - (F * (G / H)))

Answers: 1


Another question on Computers and Technology

Computers and Technology, 22.06.2019 08:00
Two technicians are discussing the common u-joint. technician a says its input and output speeds should be equal. technician b says that it normally has two yokes. which technician is correct?
Answers: 1

Computers and Technology, 22.06.2019 15:00
Atool that matches persoal skills qualities interests and talets to a career is called a
Answers: 1

Computers and Technology, 23.06.2019 08:00
What is a scenario where records stored in a computer frequently need to be checked
Answers: 2

Computers and Technology, 23.06.2019 11:00
What are the possible consequences of computer hacking? what is computer piracy? describe some examples. what are the effects of computer piracy? what are the possible consequences of computer piracy? what is intentional virus setting? describe some examples. what are the effects of intentional virus setting? what are the possible consequences of intentional virus setting? what is invasion of privacy? describe some examples. what are the effects of invasion of privacy? what are the possible consequences of invasion of privacy? what is an acceptable use policy and what is the purpose of the acceptable use policy what is intellectual property and how can you use it?
Answers: 1
You know the right answer?
Questions

History, 02.11.2020 01:40

Mathematics, 02.11.2020 01:40

Mathematics, 02.11.2020 01:40

Mathematics, 02.11.2020 01:40


Advanced Placement (AP), 02.11.2020 01:40


English, 02.11.2020 01:40

Mathematics, 02.11.2020 01:40


Arts, 02.11.2020 01:40


Mathematics, 02.11.2020 01:40

English, 02.11.2020 01:40


Mathematics, 02.11.2020 01:40

Mathematics, 02.11.2020 01:40


Mathematics, 02.11.2020 01:40