Answers: 2


Another question on Computers and Technology

Computers and Technology, 21.06.2019 22:00
Draw the hierarchy chart and design the logic for a program that calculates service charges for hazel's housecleaning service. the program contains housekeeping, detail loop, and end-of-job modules. the main program declares any needed global variables and constants and calls the other modules. the housekeeping module displays a prompt for and accepts a customer's last name. while the user does not enter for the name, the detail loop accepts the number of bathrooms and the number of other rooms to be cleaned. the service charge is computed as $40 plus $15 for each bathroom and $10 for each of the other rooms. the detail loop also displays the service charge and then prompts the user for the next customer's name. the end-of-job module, which executes after the user enters the sentinel value for the name, displays a message that indicates the program is complete.
Answers: 2

Computers and Technology, 22.06.2019 21:30
Nathan wants to create multiple worksheet containing common formatting styles for his team members. which file extension him to save these worksheets? nathan to create multiple worksheets with common styles. he needs to save them with the extension.
Answers: 1

Computers and Technology, 23.06.2019 01:30
In deadlock avoidance using banker’s algorithm, what would be the consequence(s) of: (i) a process declaring its maximum need as maximum possible for each resource. in other words, if a resource a has 5 instances, then each process declares its maximum need as 5. (ii) a process declaring its minimum needs as maximum needs. for example, a process may need 2-5 instances of resource a. but it declares its maximum need as 2.
Answers: 3

Computers and Technology, 24.06.2019 16:30
What is the item which could be matched with a statement below? software installed on a computer that produces pop-up ads using your browser an example of social engineering malware loads itself before the os boot is complete type of spyware that tracks your keystrokes, including passwords windows key + l the practice of tricking people into giving out private information or allowing unsafe programs into the network or computer when someone who is unauthorized follows the employee through a secured entrance to a room or building a type of malware that tricks you into opening it by substituting itself for a legitimate program a computer that has been hacked, and the hacker is using the computer to run repetitive software in the background without the user's knowledge an infestation designed to copy itself repeatedly to memory, on drive space, or on a network
Answers: 1
You know the right answer?
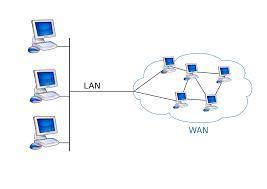
All about wide area network...
Questions

Biology, 18.09.2020 22:01

Mathematics, 18.09.2020 22:01

Computers and Technology, 18.09.2020 22:01

Mathematics, 18.09.2020 22:01

Mathematics, 18.09.2020 22:01

Mathematics, 18.09.2020 22:01

Mathematics, 18.09.2020 22:01

Mathematics, 18.09.2020 22:01

Mathematics, 18.09.2020 22:01

Mathematics, 18.09.2020 22:01

Spanish, 18.09.2020 22:01

Mathematics, 18.09.2020 22:01

Mathematics, 18.09.2020 22:01

Mathematics, 18.09.2020 22:01

Mathematics, 18.09.2020 22:01

Mathematics, 18.09.2020 22:01

Mathematics, 18.09.2020 22:01

Mathematics, 18.09.2020 22:01

Mathematics, 18.09.2020 22:01

Mathematics, 18.09.2020 22:01