Computers and Technology, 11.02.2020 03:55 martinez6221
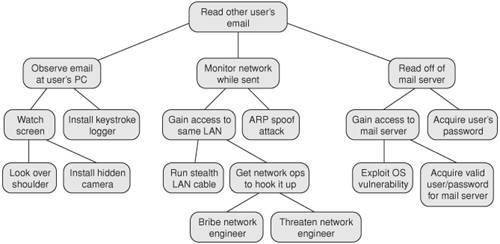
Create an attack tree for reading someone else's e-mail. Upload your document to answer this question.

Answers: 3


Another question on Computers and Technology

Computers and Technology, 22.06.2019 14:40
You are working with a professional edition organization. they wish to install the expense tracker which requires the use of 4 custom tabs, 3 custom objects, and one custom app. if the company is already using 4 applications, 36 custom objects, and 7 custom tabs, what will happen when they try to install expense tracker?
Answers: 1

Computers and Technology, 23.06.2019 12:30
How is the brightness of oled of the diaplay is controled
Answers: 1

Computers and Technology, 23.06.2019 15:10
What role did women fill during world war ii?
Answers: 1

Computers and Technology, 23.06.2019 21:00
Which set of steps will organize the data to only show foods with more than 100 calories and rank their sugar content from greatest to least?
Answers: 1
You know the right answer?
Create an attack tree for reading someone else's e-mail. Upload your document to answer this questio...
Questions

Mathematics, 28.08.2020 01:01

Mathematics, 28.08.2020 01:01






Chemistry, 28.08.2020 01:01

Mathematics, 28.08.2020 01:01


Chemistry, 28.08.2020 01:01


Mathematics, 28.08.2020 01:01

Mathematics, 28.08.2020 01:01

Business, 28.08.2020 01:01


Mathematics, 28.08.2020 01:01

Mathematics, 28.08.2020 01:01