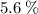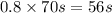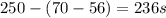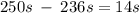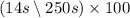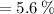Computers and Technology, 15.01.2020 05:31 Rboltonbcs
Another pitfall cited in section 1.10 is expecting to improve the overall performance of a computer by improving only one aspect of the computer. consider a computer running a program that requires 250 s, with 70 s spent executing fp instructions, 85 s executed l/s instructions, and 40 s spent executing branch instructions. 1.13.2 [5] < 1.10> by how much is the time for int operations reduced if the total time is reduced by 20%?

Answers: 2


Another question on Computers and Technology

Computers and Technology, 23.06.2019 11:30
The most accurate readings that you can take on an analog vom are when the meter's pointer is at the a. center scale. b. extreme right. c. near right. d. extreme left.
Answers: 1

Computers and Technology, 24.06.2019 04:30
1. web and mobile applications allow users to be actively engaged in an online activity. a true b false 2. some examples of business applications purposes are to collaborate, share files, meet virtually in real-time, and accept payments. a true b false 3. an education application would most likely do which of the following? a allow users to watch popular movies and tv shows b connect users with social and business contacts c confirm users' travel plans d teach users a new language 4. a uniform resource locator (url) is how the internet knows where to take users when an address is typed into a browser. a true b false 5. deon is required to provide the citation information for his sources. what type of information should he collect from his sources? a author name, title, date of publication, date of access, url b connections to background information c interesting facts and statistics d notes on important information
Answers: 1

Computers and Technology, 24.06.2019 19:20
Kiesha has a worksheet with a range of cells using the following columns: name, score, group, study group, and date. kiesha needs to sort the worksheet on the date field. which option she use to most efficiently complete this task ? a use the cut and paste option to reorganize the data to fit that order b use the filter function to organize the data based on the date c use the order function to organize the data based on the date d use the sort function to organize the data based on date order
Answers: 3

Computers and Technology, 25.06.2019 01:30
Once a vulnerability has been identified by nessus, where would you check for more information regarding the identified vulnerability, exploits, and any risk mitigation solution?
Answers: 1
You know the right answer?
Another pitfall cited in section 1.10 is expecting to improve the overall performance of a computer...
Questions






Computers and Technology, 12.08.2020 05:01








Mathematics, 12.08.2020 05:01

Mathematics, 12.08.2020 05:01


Mathematics, 12.08.2020 05:01

History, 12.08.2020 05:01