
Computers and Technology, 26.12.2019 00:31 babygirlgabby2137
One of the earlier applications of cryptographic hash functions was the storage
of passwords for user authentication in computer systems. with this method, a
password is hashed after its input and is compared to the stored (hashed) reference
password. people realized early that it is sufficient to only store the hashed versions
of the passwords.
1. assume you are a hacker and you got access to the hashed password list. of
course, you would like to recover the passwords from the list in order to impersonate
some of the users. discuss which of the three attacks below allow this.
exactly describe the consequences of each of the attacks:
attack a: you can break the one-way property of h.
attack b: you can find second preimages for h.
attack c: you can find collisions for h.
2. why is this technique of storing hashed passwords often extended by the use
of a so-called salt? (a salt is a random value appended to the password before
hashing. together with the hash, the value of the salt is stored in the list of hashed
passwords.) are the attacks above affected by this technique?
3. is a hash function with an output length of 80 bit sufficient for this application?

Answers: 2


Another question on Computers and Technology

Computers and Technology, 23.06.2019 00:30
Write the html code to make a link out of the text “all about puppies”. it should link to a pdf called “puppies.pdf” inside the “documents” folder. the pdf should open in a new window.
Answers: 2

Computers and Technology, 23.06.2019 07:10
If you want to import a picture into a dtp application, what must you do first? draw an image frame. import text. open the folder containing the file. select get image… from the windows menu.
Answers: 2

Computers and Technology, 23.06.2019 10:50
Your friend kayla is starting her own business and asks you whether she should set it up as a p2p network or as a client-server network. list three questions you might ask to kayla decide which network to use and how her answers to those questions would affect your recommendation.
Answers: 2

Computers and Technology, 24.06.2019 01:00
Mastercard managers are motivated to increase (1) the number of individuals who have and use a mastercard credit card, (2) the number of banks and other clents who issue mastercards to customers and/or employees, and (3) the number of locations that accept mastercard payments. discuss how mastercard could use its data warehouse to it expand each of these customer bases.
Answers: 3
You know the right answer?
One of the earlier applications of cryptographic hash functions was the storage
of passwords f...
of passwords f...
Questions

Business, 01.09.2021 05:20

History, 01.09.2021 05:20





Mathematics, 01.09.2021 05:20

English, 01.09.2021 05:20

Mathematics, 01.09.2021 05:20

Health, 01.09.2021 05:20



Mathematics, 01.09.2021 05:20

Mathematics, 01.09.2021 05:20


Mathematics, 01.09.2021 05:20

English, 01.09.2021 05:20

English, 01.09.2021 05:20


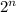 . It requires the attacker to have an idea about the kind of passwords that might be used and then brute force all of them to find string that has the same hash. Each try will have a chance of 1/
. It requires the attacker to have an idea about the kind of passwords that might be used and then brute force all of them to find string that has the same hash. Each try will have a chance of 1/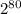 different hash values. This means there is at least one collision if
different hash values. This means there is at least one collision if 

